Welcome back, my greenhorn hackers!
Sometimes, we don't have a specific target in mind, but rather we are simply looking for vulnerable and easy-to-hack targets anywhere on the planet. Wouldn't be great if we had a search engine like Google that could help us find these targets? Well, we do, and it's called Shodan!
What Is Shodan?
Some have described Shodan as a search engine for hackers, and have even called it "the world's most dangerous search engine". It was developed by John Matherly in 2009, and unlike other search engines, it looks for specific information that can be invaluable to hackers.
Shodan pulls service banners (see my tutorial on fingerprinting web servers for more on banners) from servers and devices on the web, mostly port 80, but also ports 21 (ftp), 22 (SSH), 23 (telnet), 161 (SNMP), and 5060 (SIP).
What Can Shodan Show Us?
Since almost every new device now has a web interface (maybe even your refrigerator) to ease remote management, we can access innumerable web-enabled servers, network devices, home security systems, etc.
Shodan can find us webcams, traffic signals, video projectors, routers, home heating systems, and SCADA systems that, for instance, control nuclear power plants and electrical grids. If it has a web interface, Shodan can find it!
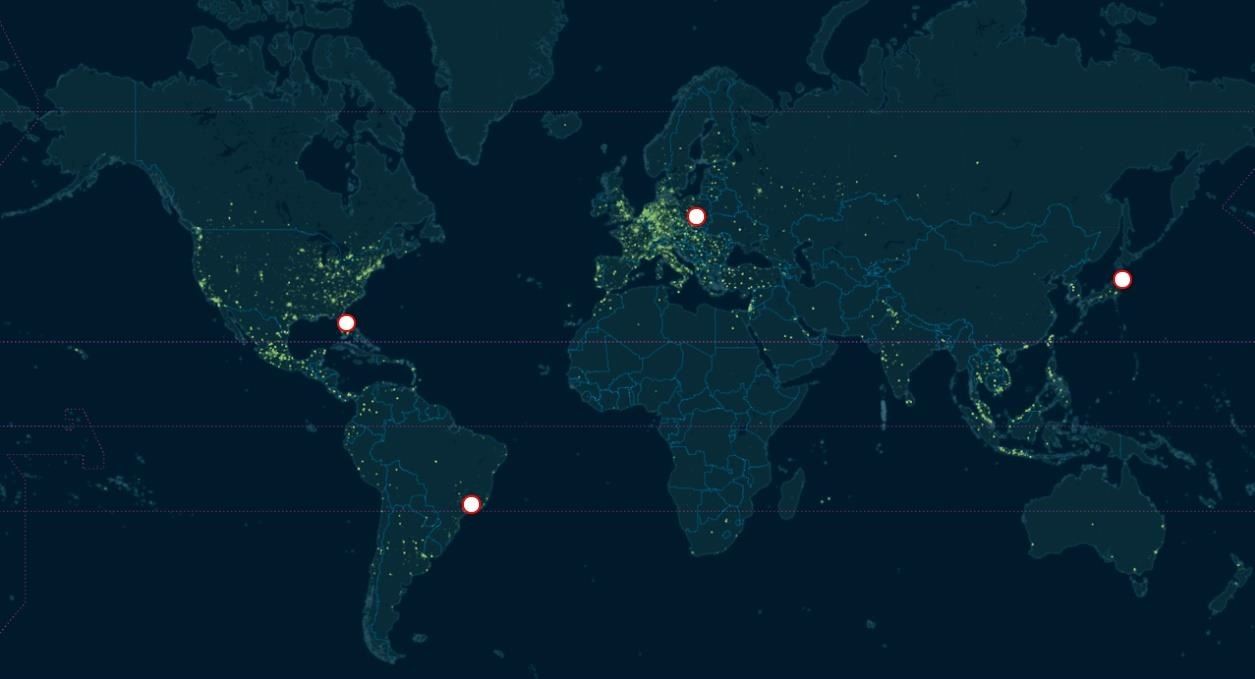
Although many of these systems communicate over port 80 using HTTP, many use telnet or other protocols over other ports. Keep that in mind when trying to connect to them.
Now let's take a look at this fascinating and nefarious search engine!
Step 1: Create a Shodan Account
First, let's start by navigating to shodanhq.com. When we do, we'll be greeted by an opening screen like that below.
Shodan requires that you register to use all of its features, but the service is free unless you need to use some of its advanced features.
Step 2: Search on Shodan
Once we have registered, we can either do custom searches or we can go to the "Search Directory" and see some of the most common and recent searches. If you are new to Shodan, I recommend that you browse "Popular Searches" first.
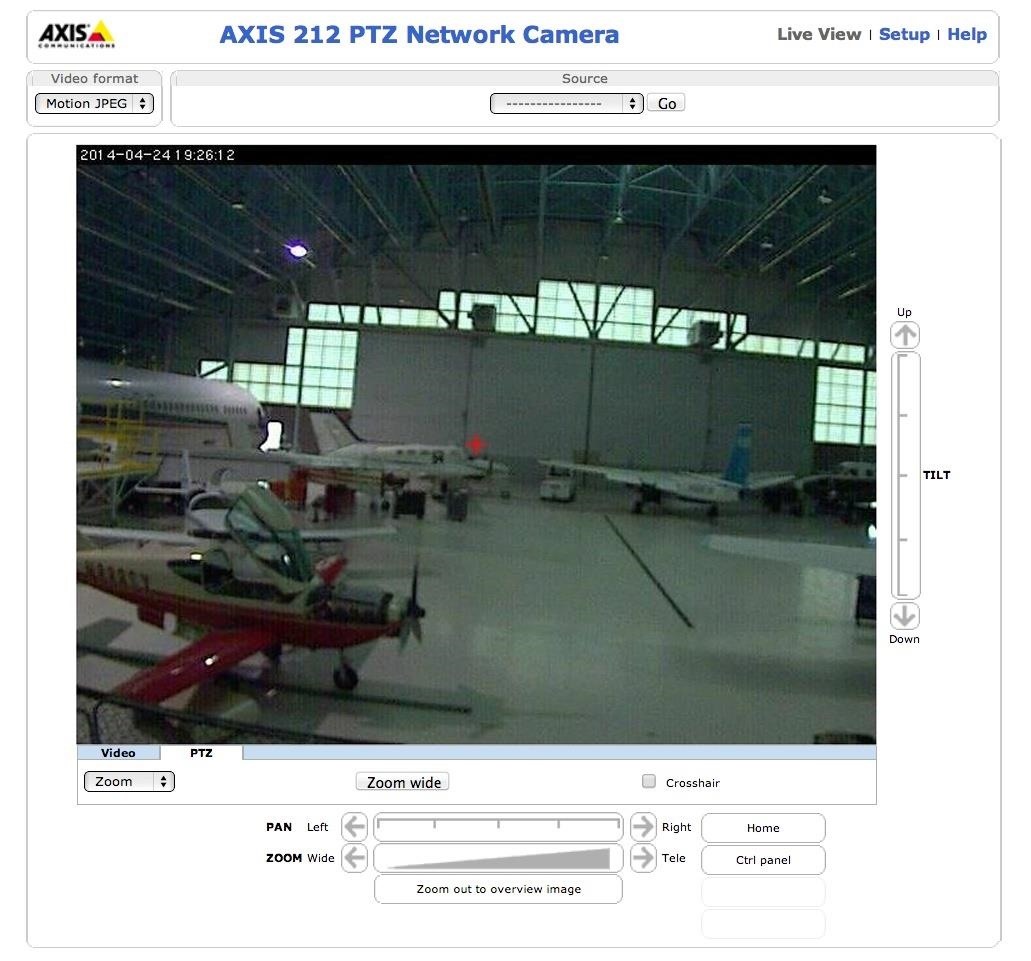
Step 3: Find Unprotected Webcams
Among the devices we can find on Shodan are innumerable, unprotected webcams. Here is one of many that I found on Shodan. This one is inside an airplane hangar in Norway. Notice that it has java controls to tilt and pan that you can use from the web so that you can scan and zoom-in throughout the hangar.
Step 4: Find Traffic Lights
There are so many devices that can be found on Shodan that the list would fill this entire article. One of the most intriguing things we can find are traffic signals and the cameras that monitor traffic at lighted intersections (some states now use these cameras to record your license plate number and send you a ticket if they detect you speeding or running a red light).
Careful here! Messing with or hacking traffic signals can cause fatalities and may be illegal. Here I show a listing of the "Red Light enforcement cameras" from Shodan.
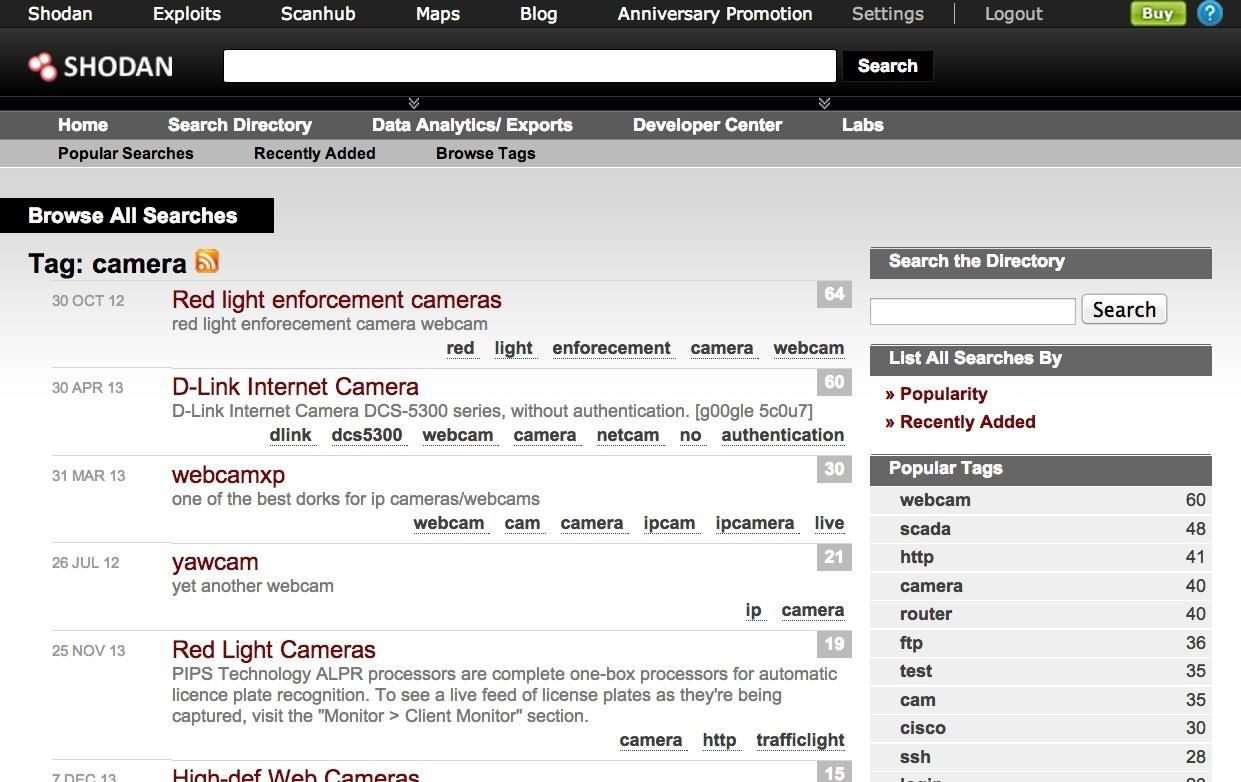
Step 5: Find Routers
Shodan catalogues thousands, if not millions, of routers, many of which are unprotected. Here's a screenshot of one I found and logged into the administrator account with the username of "admin" and password of "admin".
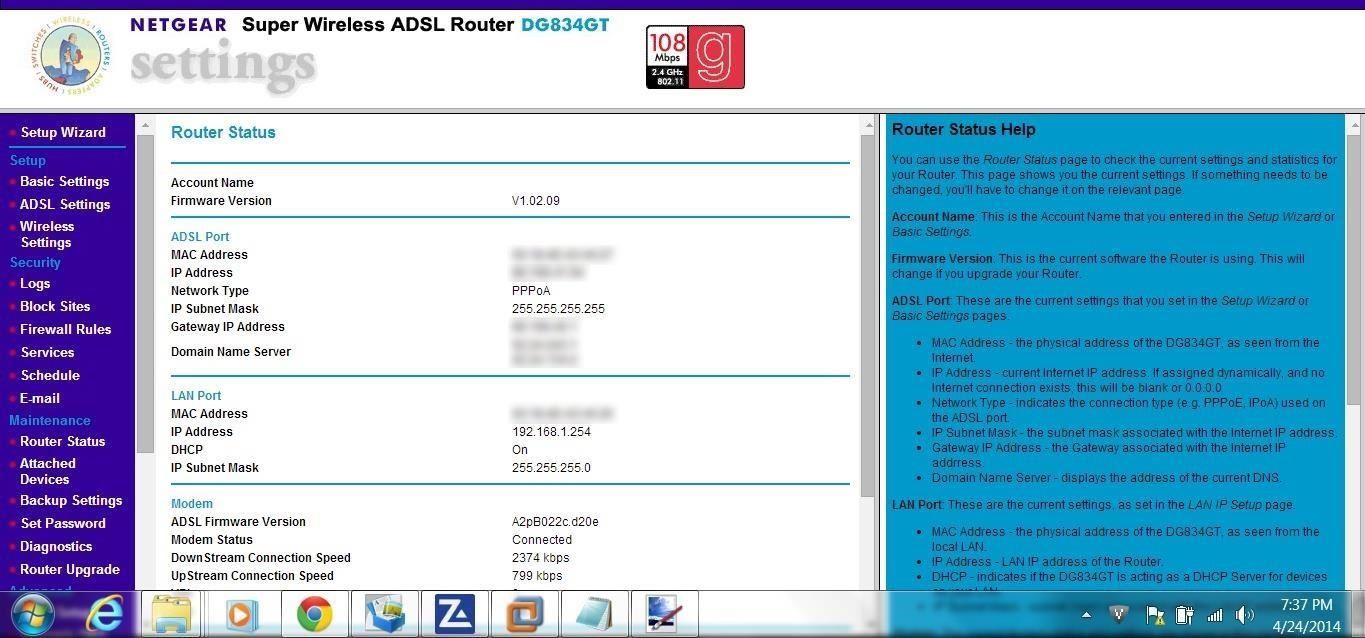
Obviously, if I had malicious intentions, I could have changed all their settings, including the password and wreaked havoc on this wireless device and its poor, unsuspecting users.
Step 6: Find SCADA Systems
Among the scariest and potentially most damaging uses of Shodan is finding SCADA (supervisory control and data acquisition) devices with web interfaces. SCADA devices are those that control such things as the electrical grid, water plants, waste treatment plants, nuclear power plants, etc.
These SCADA devices are the most likely targets in a cyber-terrorism or cyber warfare scenario, where two combatants are attempting to disable the other's infrastructure. Obviously, if one combatant can disable the others electrical grid, power and water plants, etc., it won't to take long to bring their adversary to their knees.
A cursory search of SCADA devices brought me to IP address of a hydroelectric plant in Genoa, Italy.
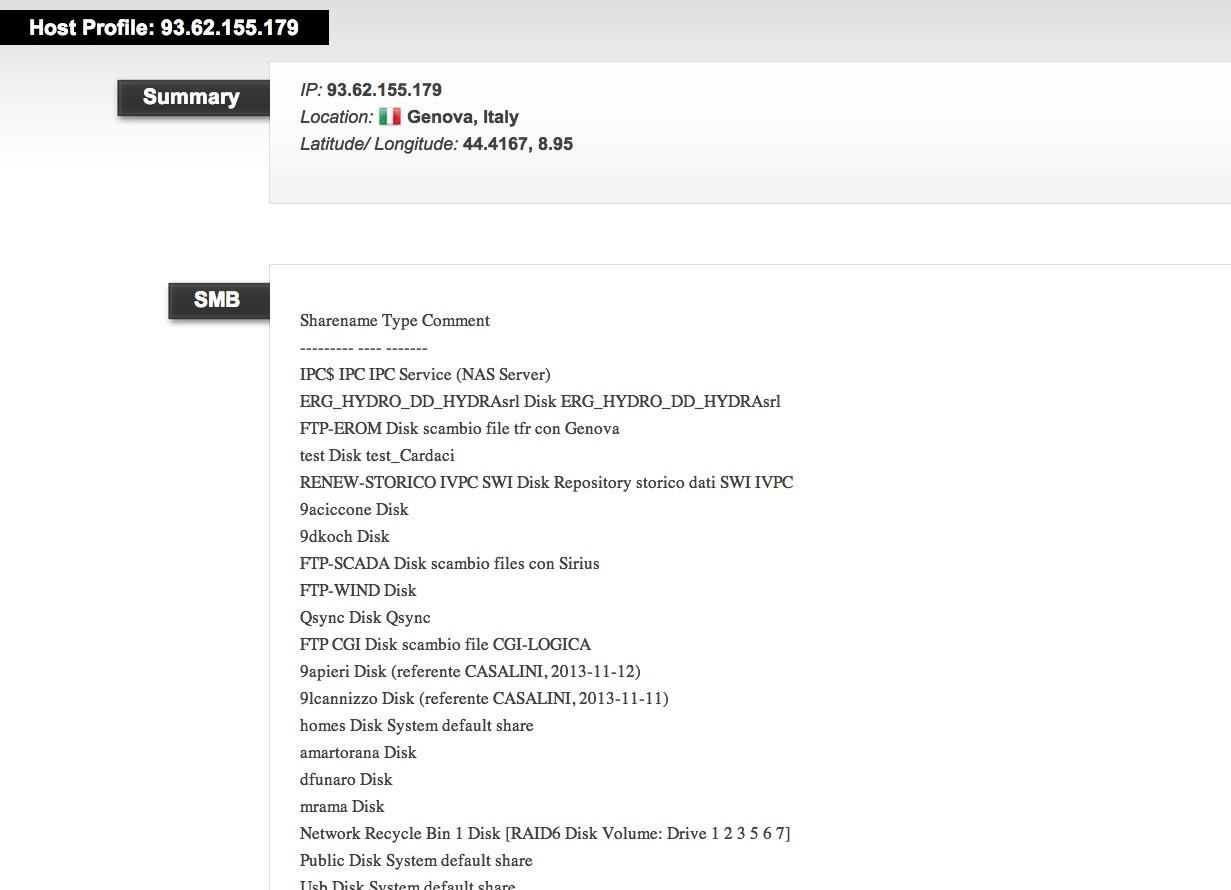
When I clicked on this link, I was presented with this login screen of the hydroelectric plant's control system's interface.
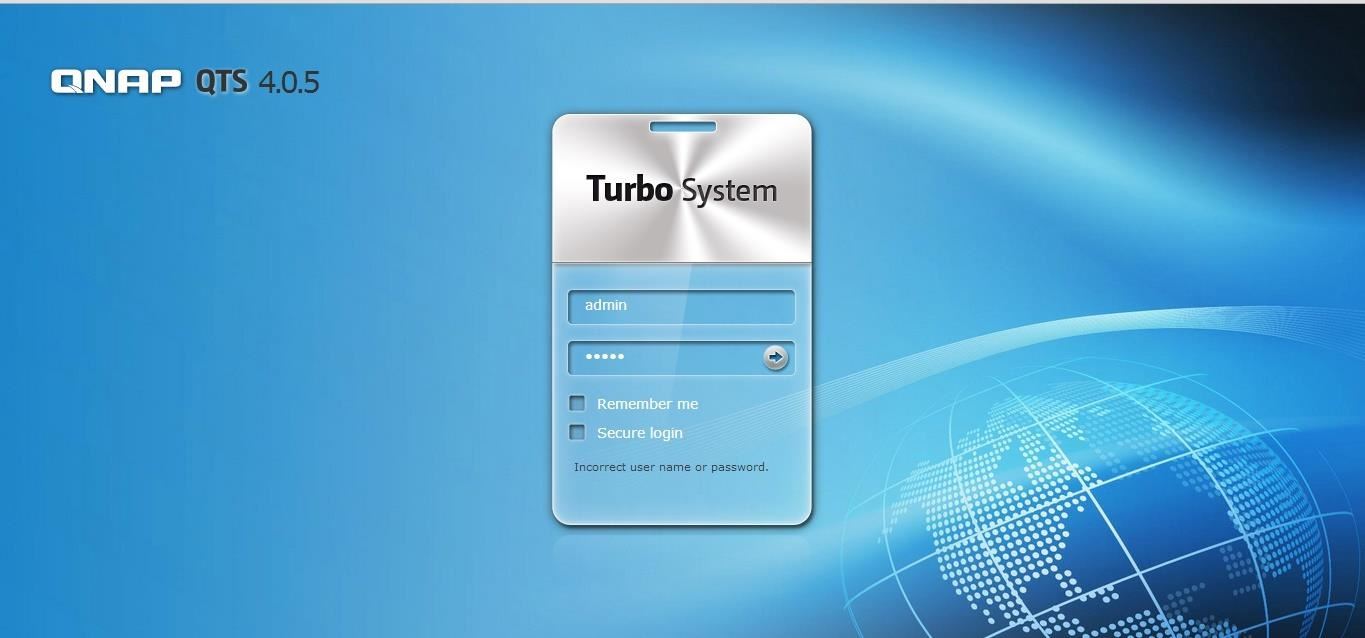
Obviously, the ability to login to this web-based interface could be very damaging to the hydro plant and the people and nation it serves.
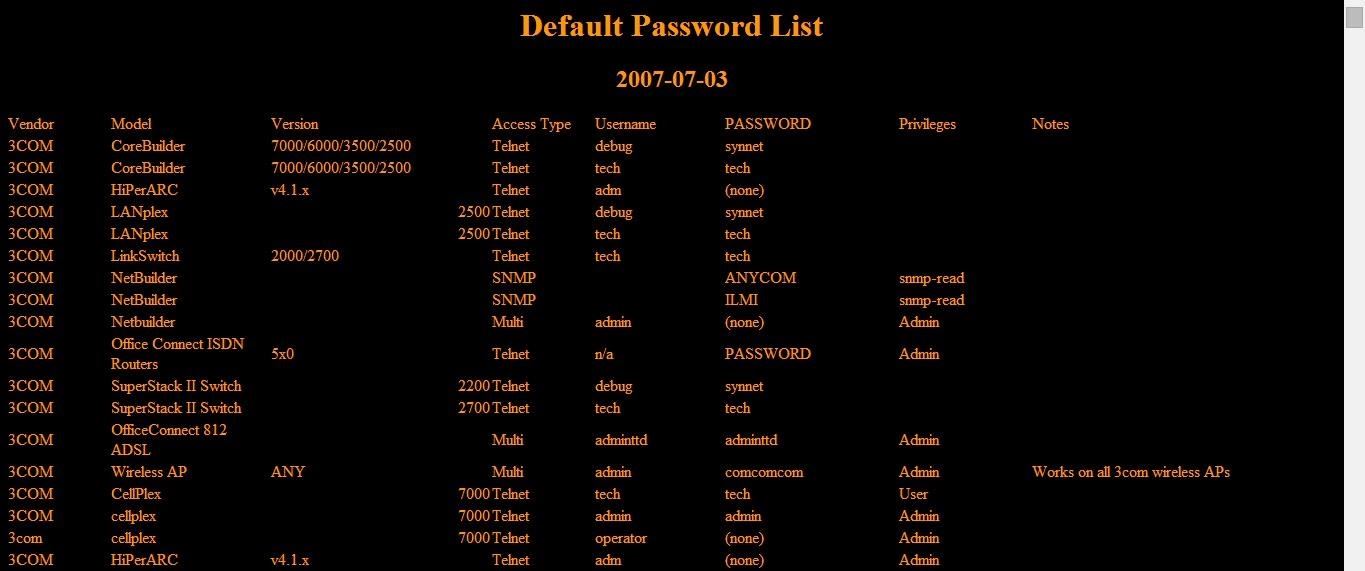
Step 7: Find the Default Passwords
Many of these sites and interfaces use default passwords. Fortunately for us, there are many resources on the web that list the default passwords for all devices. Here is one at www.phenoelit.org/dpl/dpl.html. There are literally hundreds of these sites on the web. Simply Google "default passwords".
As many consumers and system administrators are careless and don't change the default passwords, often you can gain access to these devices simply using these lists to find the default admin username and password.
Shodan Is Your New Best Friend
Shodan is a different kind of search engine. Shodan pulls banners from IP addresses and then catalogues all types of devices that have a remote interface from all over the world. Many of these devices are set to accept default logins, so that once you find a device and its default login, you may be able to own it! Just keep in mind that Shodan is not an anonymous service.
In addition, Shodan has some powerful features to search specifically for devices by type, login, port, and geography. I will show you some of these on my next Shodan tutorial, so keep coming back, my greenhorn hackers!
Just updated your iPhone? You'll find new emoji, enhanced security, podcast transcripts, Apple Cash virtual numbers, and other useful features. There are even new additions hidden within Safari. Find out what's new and changed on your iPhone with the iOS 17.4 update.






















27 Comments
awesome! 2 days ago I was thinking about it to how to use Shodan...
Thanks OTW!
OWT:
Are you psychic? I was just at the point of researching and setting up a automated mass banner search of the Internet through nmap. Omg it's good to see I don't have to now. It appears its time to fire up Tor get my dummy email address and get to work. :)
Jon:
I'm not psychic but I hacked your brain and left a rootkit in.
OTW
O.K now its making sense I have been wondering how I have gotten so much smarter.
OWT, might be a good time to look at RAT deployment, setting up and management.
Shit, this looks like a honeypot if I've ever seen one.
What do you mean, If you take precautions with your identity, its just information. Do you know what a honey pot is. There are some great articles here on what they are and how to detect them.
Ok gonna cover this real quick, I think tomorrow I will do a more in depth post, been really busy with art and researching hacking.
Do not sign up for shodan if you have any intentions what so ever and never to do anything marginally, partially or in any way that can lead back to you with your regular account.
If you wanna play it safe:
Place Tor on a thumb drive, sd card whatever and run it from there.
Through Tor setup a hushmail account. (working on some better solutions I think through I2p but this will work for now). Do not use any information that you have ever, ever used anywhere to setup the account.
Sign up through Tor (and preferable though a proxy server) To Shodan.
Only use Shodan through your Tor browser. (I personally only bookmark all sites I want to access that may cause be problems in my Tor browser.) This way if I am drunk or being stupid I know I am not a secure browser.
:)
MASTER OTW IS IT SAFE TO USE IT? AND CAN YOU TEACH US HOW TO FIND EXPLOITS TO HACK TRAFFIC LIGHTS ETCETERA? PUBLIC CAMERAS ETC?
Dragon:
Many of these sites have no protection. All you need to do is login with the default user and password. If that doesn't work, then it becomes a password cracking problem. No exploits needed.
OTW
nice
but please, how can i perform a kind of search e.g: need shodan to search for vul cam in my area
Horls:
I'll be following up shortly with a second part on how to do specific searches.
OTW
okay, will be expecting that. thank u
Dear otw
I was wondering how i could find exampel my schools camera, or i could use it to spy on my friends webcam???
Good tutorial, but i can only look at boring webcams... All others got a password, how can i watch webcams in my own country (denmark)
Anonymous:
Have you read my second Shodan tutorial? I'll be my next Shodan tutorial on finding web cams.
OTW
Can we use any other search engines to find results similar to the shodan results ?
Yes you can. You just need to dork it. Got Metasearch Engine?
wow
i have access to my friend ipcam but the video wont show up they say plugin and adobe flash problem ...i wonder how i can fix it i used both chrom and mozila firfox
and what browser u use thnx
Update your Adobe Flash player
i already did :( i geuss the problem is in the browser or smtg
i m not able to find any webcams with default pass..can u provide me URL for any webcam which has default pass
thx OTW..i found 2
grte article; however, still struggling to wrk out how you got all those search results.
How do you scan for NEARBY traffic signs?
Share Your Thoughts